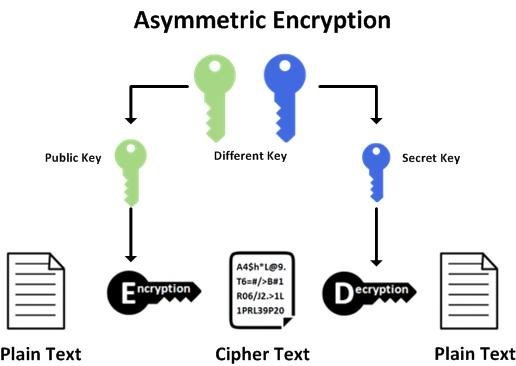
When we create Unix / Linux instances in the cloud (regardless of the provider we usually use), we are asked to use a public / private key set to secure access to the instances. Without this additional protection and only relying on a Login / Password, our systems are vulnerable to dictionary attacks or brute force, which depending on the strength of our password will delay more or less our atrackers.
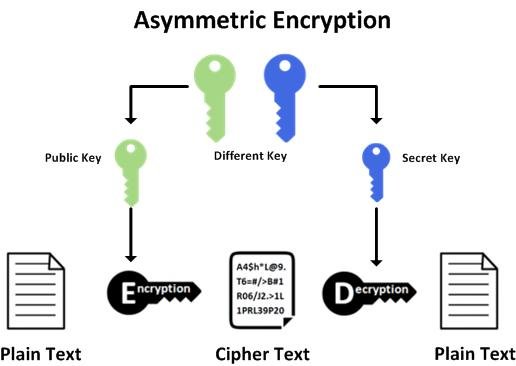
Usually when we generate our keys, we don't worry too much and assume that Keys are in itself secure.
but the reality is that depending on the options we choose when creating it, these will be more or less robust.
The passphrase is important:
The passphrase is very important, because it will be used to encrypt the Private Key, so if someone obtains this Private Key, it still will be protected. The passphrase must be cryptographically strong.
If you don't know howto generate a strong passphras, you can find a random generator here.
Choosing the algorithm right Key Size:
Well yes, we have several options of which the most common are:
- RSA => It is a fairly old algorithm, which relies on the difficulty of factoring large numbers. You should not under any circumstances use a key lower than 2048 bits, if you can, 4096 is a much better option. The strong point of this algorithm is compatibility, since (mainly due to its age) it is widely supported.
- DSA=> another old rocker, in this case developed by the United States government and based on the difficulty of processing logarithms. A key length of 1024 is usually used and unless you have no other option, it doesn't provide many advantages to use it, neither in security or in compatibility.
- ECDSA=>it is a relatively new algorithm also developed by the United States government. It bases its strength on the calculation of elliptical curves and it is probably a good option today. Against it, saying that it uses small key lengths (256, 384 and 521), so I would recommend always using the 521 option. Regarding portability, most SSH clients already support it.
- ED25519=>This algorithm was recently added to OpenSSH and its main drawback is that it is supported by customers. It is a recommended option if our systems support it.
ssh-keygen -t rsa -b 4096 ssh-keygen -t dsa ssh-keygen -t ecdsa -b 521 ssh-keygen -t ed25519
Which one do I use??
Well, I mainly use RSA 4096 and ed25519 depending on what the systems support. If you don't want to complicate a 4096 RSA it will give you good security and excellent portability. If you don't distrust that it is developed by the government, ECDSA is also an excellent option.
I hope you have found it of interest!!!